Viruses and worms are a cause for thousands of losses all over the world. There are number of viruses and worms created. Below i have listed 6 most dangerous and havoc creating viruses that affected millions of computer users over the world. The order of viruses is not important.
Most dangerous computer viruses :
1. ILOVEYOU :
This ILOVEYOU worm is considered to be most dangerous worm ever created. It was written in VBScript. It was first noticed in Philippines on May 4 2000 and then spread all over world in just one day, affecting 10% internet users and causing loss of about $5.5 billion. The worm arrived in email inbox with subject “ILOVEYOU”. Hence, called ILOVEYOU worm. It had an attachment “LOVE-LETTER-FOR-YOU.TXT.vbs” . The worm overwrote many important files, with music, multimedia files with a copy of itself attached to each file. Also, it sent the worm to everyone on victim contact list. Thus, worm spread very fast. Only windows users were affected.
2. Mydoom :
Mydoom , a computer virus affected Microsoft Windows. After it was first noticed on January 26, 2004, it became fastest spreading computer virus ever, breaking record of Sobig worm. Mydoom was designed to send junk emails from infected computers. The actual worm programmer is still unknown.
3. Virut virus :
This Virut virus infects executable portable files such as .exe and .scr andeach time it propagates it uses Polymorphism - to evade detection. On infected machine, virus opens a backdoor connecting with an IRC server which is prespecified by virus programmer. This backdoor allow attacker to download additional malware to victim computer. This virus affected and shut down court system computers of Texas this February.
4. Blaster worm :
This Blaster worm - a computer worm that affected computers running Microsoft operating systems. But, the spread of this worm was limited by filtering of ISP and its publicity. The worm was designed to start a SYN Flood on Aug 15, 2003 against port 80 of windowsupdate.com, intended to create a distributed DDoS attack against this site.
If the worm detects an internet connection, the system would become unstable and after displaying a message for 60 seconds, the system used to restart. The message displayed looked like:
“I just want to say LOVE YOU SAN!!”
“billy gates why do you make this possible? Stop making money
and fix your software!!”
5. Sobig worm :
This worm ws detected in Aug 2003 which affected millions of internet connected windows operating systems. The worm was written using Microsoft Visual C++ compiler and compressed using tElock. The most destructive version was Sobig.F .
This worm was worm as it replicated itself and also a Trojan Horse as it appeared other than malware. The programmer of this worm is still not known.
6. Conficker virus :
This virus came into role in November 2008 and affected millions of computer. Basically, its a worm capable of replicating itself and thus can spread fast. The worm spreads itself primarily through a buffer overflow vulnerability in the Server Service on Windows based computers.
When this worm is executed on a computer, it is capable of disabling Windows services such as Windows Update, Windows Defender, Windows Security Center and even Windows Error reporting.
But, the threat due to this worm is reduced as most anti viruses are now detecting this worm and its further spread is thus prevented. This worm is mainly spreading in China, followed by Argentina, Brazil, Russia, and India - where software update is done to less extent.
So friends, this is all about viruses. These are most dangerous viruses or worms that affected millions of worldwide computers. I just wanted to say that keep your anti viruses updated to prevent yourself from being affected by such viruses and worms. If you think any other virus or worm needs mention over here, please mention it in comments section. I will update the article.
Source: http://computer-bloggingtricks.today.com/2009/03/12/6-ever-most-dangerous-computer-pc-viruses-and-worms/
Most dangerous computer viruses :
1. ILOVEYOU :
This ILOVEYOU worm is considered to be most dangerous worm ever created. It was written in VBScript. It was first noticed in Philippines on May 4 2000 and then spread all over world in just one day, affecting 10% internet users and causing loss of about $5.5 billion. The worm arrived in email inbox with subject “ILOVEYOU”. Hence, called ILOVEYOU worm. It had an attachment “LOVE-LETTER-FOR-YOU.TXT.vbs” . The worm overwrote many important files, with music, multimedia files with a copy of itself attached to each file. Also, it sent the worm to everyone on victim contact list. Thus, worm spread very fast. Only windows users were affected.
2. Mydoom :
Mydoom , a computer virus affected Microsoft Windows. After it was first noticed on January 26, 2004, it became fastest spreading computer virus ever, breaking record of Sobig worm. Mydoom was designed to send junk emails from infected computers. The actual worm programmer is still unknown.
3. Virut virus :
This Virut virus infects executable portable files such as .exe and .scr andeach time it propagates it uses Polymorphism - to evade detection. On infected machine, virus opens a backdoor connecting with an IRC server which is prespecified by virus programmer. This backdoor allow attacker to download additional malware to victim computer. This virus affected and shut down court system computers of Texas this February.
4. Blaster worm :
This Blaster worm - a computer worm that affected computers running Microsoft operating systems. But, the spread of this worm was limited by filtering of ISP and its publicity. The worm was designed to start a SYN Flood on Aug 15, 2003 against port 80 of windowsupdate.com, intended to create a distributed DDoS attack against this site.
If the worm detects an internet connection, the system would become unstable and after displaying a message for 60 seconds, the system used to restart. The message displayed looked like:
“I just want to say LOVE YOU SAN!!”
“billy gates why do you make this possible? Stop making money
and fix your software!!”
5. Sobig worm :
This worm ws detected in Aug 2003 which affected millions of internet connected windows operating systems. The worm was written using Microsoft Visual C++ compiler and compressed using tElock. The most destructive version was Sobig.F .
This worm was worm as it replicated itself and also a Trojan Horse as it appeared other than malware. The programmer of this worm is still not known.
6. Conficker virus :
This virus came into role in November 2008 and affected millions of computer. Basically, its a worm capable of replicating itself and thus can spread fast. The worm spreads itself primarily through a buffer overflow vulnerability in the Server Service on Windows based computers.
When this worm is executed on a computer, it is capable of disabling Windows services such as Windows Update, Windows Defender, Windows Security Center and even Windows Error reporting.
But, the threat due to this worm is reduced as most anti viruses are now detecting this worm and its further spread is thus prevented. This worm is mainly spreading in China, followed by Argentina, Brazil, Russia, and India - where software update is done to less extent.
So friends, this is all about viruses. These are most dangerous viruses or worms that affected millions of worldwide computers. I just wanted to say that keep your anti viruses updated to prevent yourself from being affected by such viruses and worms. If you think any other virus or worm needs mention over here, please mention it in comments section. I will update the article.
Source: http://computer-bloggingtricks.today.com/2009/03/12/6-ever-most-dangerous-computer-pc-viruses-and-worms/
 A Trojan Horse Virus is a common yet difficult to remove computer threat. This is a type of virus that attempts to make the user think that it is a beneficial application.
A Trojan Horse Virus is a common yet difficult to remove computer threat. This is a type of virus that attempts to make the user think that it is a beneficial application.
 This post provide virus protection tips to protect your computer. Have Spy Sweeper scan other hard drives or removable devices for spyware and adware
This post provide virus protection tips to protect your computer. Have Spy Sweeper scan other hard drives or removable devices for spyware and adware A trial version of Microsoft's liberated anti-virus code has been launched in the US, China, Brazil, and Israel.
A trial version of Microsoft's liberated anti-virus code has been launched in the US, China, Brazil, and Israel. The “Conficker” worm / virus also known as “Downadup” infection, is actually a virus code programmed in such a way that it can infect your computer and spread itself to other computers across a network automatically, without human interaction.
The “Conficker” worm / virus also known as “Downadup” infection, is actually a virus code programmed in such a way that it can infect your computer and spread itself to other computers across a network automatically, without human interaction.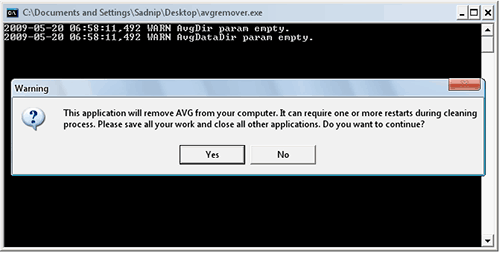 This post provide further information about AVG antivirus support. AVG Remover utility removes all parts of AVG installation on your computer, including registry items, installation and user files on your disk, etc. AVG Remover is the least option to be used in case the AVG uninstallation / repair installation process has failed repeatedly.
This post provide further information about AVG antivirus support. AVG Remover utility removes all parts of AVG installation on your computer, including registry items, installation and user files on your disk, etc. AVG Remover is the least option to be used in case the AVG uninstallation / repair installation process has failed repeatedly. Boot-sector viruses infect computer systems by copying code either to the boot sector on a floppy disk or the partition table on a hard disk. During startup, the virus is loaded into memory. Once in memory, the virus will infect any non-infected disks accessed by the system. Examples of boot- sector viruses are Michelangelo and Stoned.
Boot-sector viruses infect computer systems by copying code either to the boot sector on a floppy disk or the partition table on a hard disk. During startup, the virus is loaded into memory. Once in memory, the virus will infect any non-infected disks accessed by the system. Examples of boot- sector viruses are Michelangelo and Stoned. Spyware is one of the biggest scourges of personal computing today especially as more and more computers are interconnected via the Internet and local area networks. If your computer is connected to a network or the Internet then you are not safe from this problem.
Spyware is one of the biggest scourges of personal computing today especially as more and more computers are interconnected via the Internet and local area networks. If your computer is connected to a network or the Internet then you are not safe from this problem.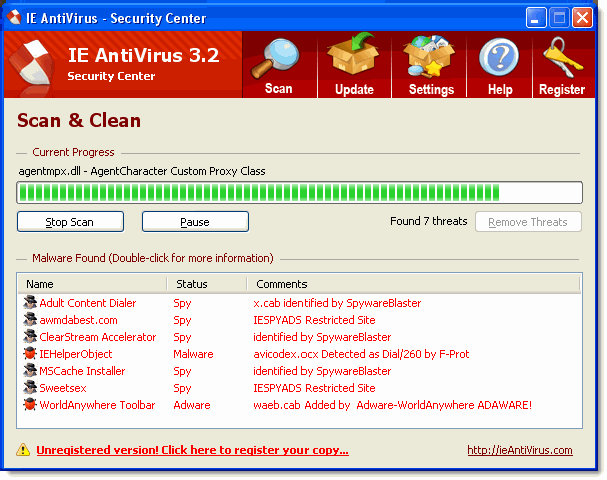

 A computer virus is a computer program that can copy itself and infect a computer without permission or knowledge of the user. The term "virus" is also commonly used, albeit erroneously, to refer to many different types of malware and adware programs. The original virus may modify the copies, or the copies may modify themselves, as occurs in a metamorphic virus. A virus can only spread from one computer to another when its host is taken to the uninfected computer, for instance by a user sending it over a network or the Internet, or by carrying it on a removable medium such as a floppy disk, CD, or USB drive. Meanwhile viruses can spread to other computers by infecting files on a network file system or a file system that is accessed by another computer. Viruses are sometimes confused with computer worms and Trojan horses.
A computer virus is a computer program that can copy itself and infect a computer without permission or knowledge of the user. The term "virus" is also commonly used, albeit erroneously, to refer to many different types of malware and adware programs. The original virus may modify the copies, or the copies may modify themselves, as occurs in a metamorphic virus. A virus can only spread from one computer to another when its host is taken to the uninfected computer, for instance by a user sending it over a network or the Internet, or by carrying it on a removable medium such as a floppy disk, CD, or USB drive. Meanwhile viruses can spread to other computers by infecting files on a network file system or a file system that is accessed by another computer. Viruses are sometimes confused with computer worms and Trojan horses.